Kuetzal database exposed: 4722 investor data at risk
An anonymous Telegram user “J“ claims to have a copy of Kuetzal database and gave a preview of it in “KuetzalDiscussion“ channel. So let’s have a look inside.
Database: kuetzal_db, Table: site_admins
As you can see, there were 6 admin accounts and 2 of those were connected to supreme.lv - my guess is that this was the web development company who created the technical solution behind Kuetzal P2P platform.
If this data is real, then it shows that either the developers of Kuetzal were super incompetent or did not care about security at all, or both. There are 2 big issues here:
Passwords were encrypted with MD5 algorithm, which is not safe. Instead SHA1 should be used or a different solution.
Two account passwords were “adminadmin“ - that is almost as smart as setting admin password to “password“ or “123456”. WTF?
And seems like the CEO had received warnings about security problems as well:
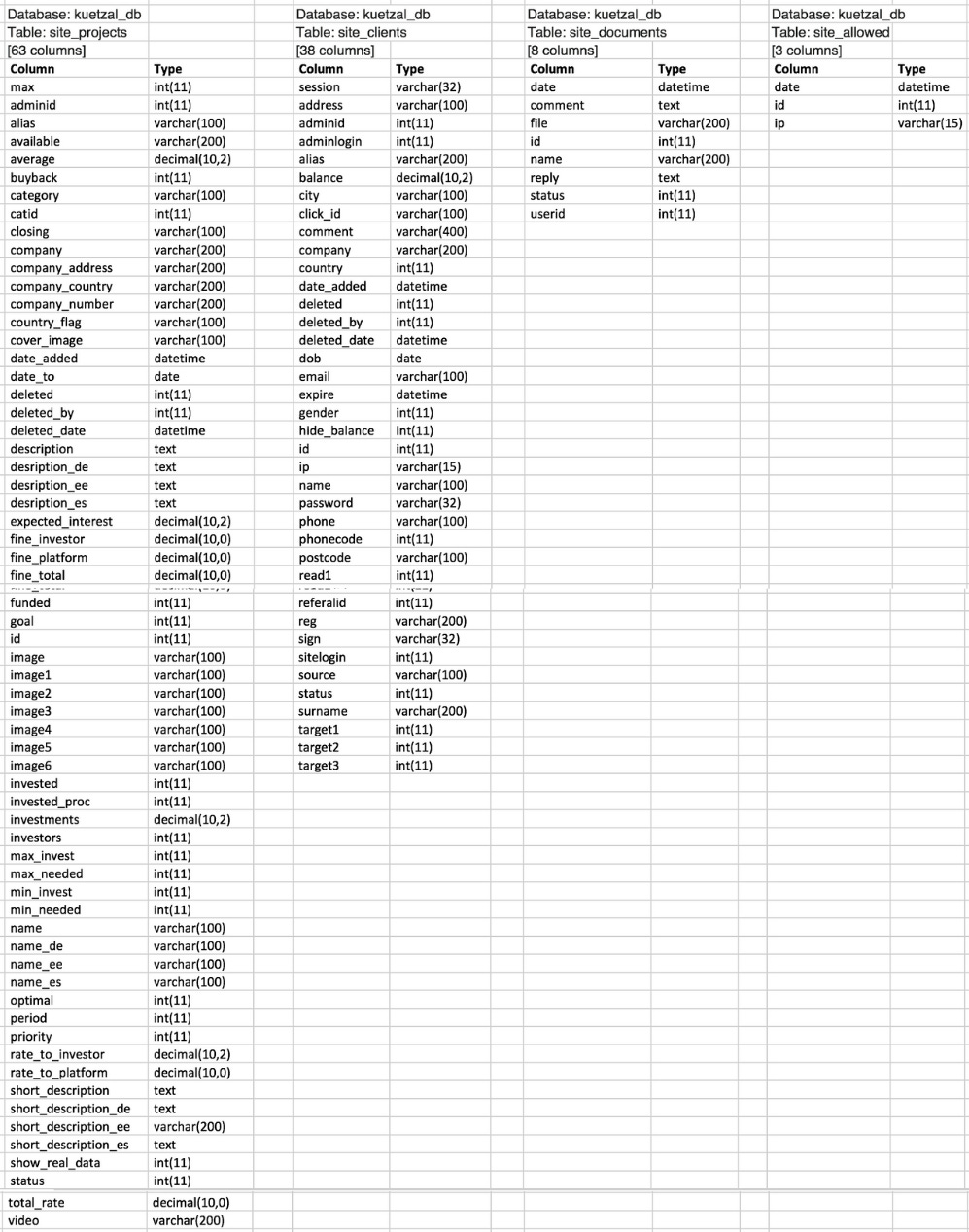
Other tables: site_projects, site_clients, site_documents, site_allowed
Full data from these tables was not shared (yet), but by column names you can see what was stored in Kuetzal database. For investors the most worrying tables are “site_clients“ and “site_documents“.
How many investors were there?
SELECT count(*) FROM site_clients: '4722'
This shows that there were 4722 “clients“ (investors) in Kuetzal database.
What documents were saved in site_documents table?
SELECT * FROM site_documents WHERE userid = XXX [2]:
[*] 2019-05-13 15:42:10, , Paspoort_XXX.jpg, 452, Pasport XXXXXXXXXX, , 1, XXX
[*] 2019-05-14 09:35:02, , thumbnail_IMG_XXXXXXX.jpg, 469, Proof of residency, , 1, X
SELECT distinct count(userid) FROM site_documents WHERE status =1: '5708'
Here you can see references to files that investors uploaded to prove their identity - in this case: passport and proof of residency. These files were not stored in the database, but on Kuetzal server and at this point there is no info, if “J“ downloaded also all the files or only the database.
In total 5708 investor documents were uploaded and stored on Kuetzal server.
Another table that was shared is site_allowed - these look like IP addresses from which admin's were allowed to login:
White list of IP addresses
SELECT ip FROM site_allowed [71]:
87.110.234.21
87.110.175.121
213.226.141.208
83.99.236.39
83.99.231.140
78.84.24.42
80.89.79.135
88.135.146.65
213.226.141.134
109.167.201.3
213.226.141.105
87.110.171.191
77.219.0.156
77.219.11.173
109.73.97.5
213.226.141.121
77.219.14.67
46.109.193.234
91.105.16.197
77.219.7.147
194.34.132.137
194.34.132.119
194.34.132.141
77.219.6.42
194.34.132.115
194.34.132.125
178.247.136.114
77.219.0.45
77.219.0.51
213.226.141.224
80.89.76.237
77.219.15.147
213.226.141.40
213.74.252.59
91.129.99.241
77.219.2.253
178.246.226.148
213.226.141.176
194.34.132.116
91.129.110.226
194.34.132.107
91.129.96.176
94.55.160.162
194.34.132.132
194.34.132.136
194.34.132.222
194.34.132.121
80.89.78.147
194.34.132.129
91.129.105.204
194.34.132.118
194.34.132.117
80.89.77.39
91.129.106.104
194.34.132.133
194.34.132.127
77.219.10.211
77.219.9.131
194.34.132.123
77.219.0.8
77.219.7.184
77.219.8.114
77.219.6.91
77.219.12.104
213.226.141.119
91.129.98.42
194.34.132.114
77.219.14.99
77.219.15.198
194.34.132.112
77.219.10.78
You can analyse them with tools like InfoByIp.com or ipapi and see that mostly these are Latvian IP addresses, but some of them are also from other countries:

Messages sent to Kuetzal were saved in database as well:
SELECT * FROM site_contacts ORDER BY date DESC [3]:
[*] 2020-01-07 23:04:57,
Hi,
I request buyback of all my investments in Kuetzal:
Goodville : 1055
Green Dev â Pyrolysis and Distillation systems : 1002
Spilve Twinhouse : 1005
Total poker : 552.25
thanks
regards
Stefano, XXX@gmail.com, XXX, XXX, +3934XXX, buyback request[*] 2020-01-07 22:57:42,
Hi,
I request buyback of all my investments in Kuetzal:
Crypto-mining container #2 : 400
Goodville : 110
Tokyo 55 : 400
VV line : 400
thanks
regards
Alessandra, XXX@gmail.com, 14548, Alessandra XXX, +393XXX, buy back request[*] 2020-01-07 21:15:05,
I have done withdrawal id XXX, but i cant see it in my bankaccount., XXXjanpaa@hotmail.com, XXX, XXX, +35840XXX, Id XXX
There are payments stored in database with future dates, up to year 2022:
SELECT date, amount, id, projectid, status, userid FROM kuetzal_db.site_projects_pays ORDER BY date DESC
SELECT * FROM site_projects_pays ORDER BY date DESC [3]:
[*] 2022-03-13 00:00:00, 154.17, 151, 1, 0, 0
[*] 2022-02-13 00:00:00, 154.17, 150, 1, 0, 0
[*] 2022-01-13 00:00:00, 154.17, 149, 1, 0, 0
SELECT * FROM site_projects_pays LIMIT 3 [3]:
[*] 2019-04-13 00:00:00, 154.17, 116, 1, 1, 0
[*] 2019-05-13 00:00:00, 154.17, 117, 1, 1, 0
[*] 2019-06-13 00:00:00, 154.17, 118, 1, 1, 0
Total amount invested?
select sum(amount) from site_transactions where type =1
8661979.57
If this number is accurate, then investors in total have invested 8,6 million EUR in Kuetzal, but I would not be surprised if the number is actually much lower and part of money “invested“ into projects is fake.
Did Kuetzal admins participate in investing?
SELECT date, adminid, amount, balance, canceled, comments, date_add, exported, friendid, id, type, userid FROM kuetzal_db.site_transactions ORDER BY id DESC LIMIT 3
SELECT * FROM site_transactions ORDER BY date DESC LIMIT 5 [5]:
[*] 2020-01-11, 36, 400.00, 424.99, 0, , 2020-01-11 15:53:21, 2, 0, XXX, 1, 48 XXX
[*] 2020-01-11, 36, 400.00, 424.99, 0, , 2020-01-11 15:53:21, 2, 0, XXX, 1, 48 XXX
[*] 2020-01-11, 36, 1000.00, 1292.17, 0, , 2020-01-11 15:46:22, 2, 0, XXX, 1, XXX
[*] 2020-01-11, 36, 300.00, 300.00, 0, , 2020-01-11 15:46:49, 2, 0, XXX, 1, 91 XXX
[*] 2020-01-11, 36, 1000.00, 1292.17, 0, , 2020-01-11 15:46:22, 2, 0, XXX, 1, XXX
It is not clear to me if these are incoming or outgoing transactions, but it looks like that the admin with user “next“ and email “info@kuetzal.com“ either made withdrawals or “invested“, these 5 transactions are all from January 11th, 2020 - so just before Kuetzal was shut down.
How did law-enforcement agencies react to this?
After creating this post, I got a message from “J“ or someone claiming to be him:
I had informed several Dutch (NL) agencies; FIOD, TCI and had a telephone conversation and email-chain with the local police.
FIOD and TCI were not interested at all. From the Estonian police I received no response at all.
Local police was more helpful and did their best to forward the case to a specialised Financial Unit. I wrote a very detailed email on the case and made clear to them, that it was important to act fast on the server / evidence as their window of opportunity was closing fast. I also made clear that I had full access to the data and I shared several data-snippets.
I also had several other Dutch victims inform them to verify I was not the only victim and there was a real case.In several followups emails, I also informed them on the Envestio 'bankrun' and details of the disaster in the making.
I finally received a reply from the specialised unit on Jan 23:Ik heb uw mail die mij via collega XXX is doorgezonden gelezen en zie dat hier sprake is van een in allerlei vormen veelgebruikte methode om geld bij investeerders op te halen. De overeenkomst in die zaken is dat de meeste gegevens fake zijn en/of niet traceerbaar en dat het geld supersnel wordt weggemaakt. Om deze reden en omdat dergelijke zaken met andere zaken moeten concurreren is de kans uitermate klein dat een politieteam deze zaak op zal gaan pakken. En dat geldt eerlijkheidshalve ook voor het fraudeteam van de politie Oost-Brabant.
Toch wil ik u vragen om aangifte te doen. Ik adviseer u om dat kort en bondig schriftelijk te doen en daarbij een lijst te maken van de contactgegevens die een rol hebben gespeeld om u over te halen om geld over te maken met zoveel mogelijk tijdstippen. Ik heb zojuist uw voicemail ingesproken; mocht u nog een telefonische toelichting willen dat kunt u mij bellen op onderstaand nummer.
Met vriendelijke groet,
Harry XXX
Operationeel Specialist D
Financiële Opsporing en Financieel Economische Criminaliteit
What can investors do?
Not much, hope & pray that their data is not shared or sold. Or have some fun:


Key takeaways
Kuetzal’s IT security was bad, CEO was informed, but did not care
Kuetzal team might have done damage to themselves as well - info about their IP addresses have been exposed, and the whole database might get shared later as well
At least 1 person claims to have full Kuetzal database, no info about investor documents
4722 investor data might get exposed or sold - no leaks yet, but if 1 person got hands on that, there could be others as well
If you invest in a P2P platform, you might not only lose your investment, but in some cases - also your data
Law-enforcement agencies were informed about potential data leaks before Kuetzal was shut down, but according to info provided to me - none of them showed big interest to act fast
Want to get access to exclusive content? Become a paid subscriber:
Or join “High-risk investments“ Telegram group for an informal discussion.